Cyber threats real for industrial automation systems
4 mins
The introduction of Internet of Things (IoT) into industrial automation environments, in the name of progress, has brought on both operational efficiencies and security risks previously unseen to the manufacturing, engineering, and mining industries. This article explains the risk drivers behind Operational Technology (OT) systems and the need for comprehensive security across the enterprise’s operations: from IT Security to Industrial Cyber Security.
IT: Meet OT
The ability to connect Information Technology (IT) systems with Operational Technology (OT) systems, such as Supervisory Control and Data Acquisition (SCADA) systems and Programmable Logic Controllers (PLCs), gives businesses access to information for a comprehensive picture of what is happening across the enterprise’s operations. It also comes with considerable IT and OT security-related risks that can have a far-reaching impact on the organisation.
“When we think about IT security, we tend to think of corporate networks, data and emails. However, the high level of connectivity that is available to companies today means that industrial, engineering and building automation systems can also be exposed to cyber security threats. The malicious worm, Stuxnet, for example, was designed to specifically target industrial Programmable Logic Controllers (PLCs), which modified their coding and gave unexpected commands to the control system. The consequence of Stuxnet was that the entire manufacturing operation was brought to a standstill for days until the IT and OT vulnerabilities were remediated.
How does OT Security differ from IT Security?
IT security strategies tend to focus on data protection and to follow the objectives of the ‘C-I-A’ model: Data Confidentiality, Integrity and Availability. However, for most OT systems, cybersecurity is not about ‘data’ but the continuity of industrial processes. So, in terms of the C-I-A model, ‘availability’ is the primary focus of security strategies as applied to OT. This is what distinguishes industrial cybersecurity needs from those of other systems, meaning that the even most effective classical IT cybersecurity solution is inappropriate for use on OT systems, putting the availability (and in some cases the integrity) of processes at risk.
IoT: connecting networks, integrating security risks
“When integrated systems aren’t adequately segregated and protected against threats like these, the whole enterprise is exposed, with potentially far-reaching consequences,” says Charl Ueckermann, CEO at AVeS Cyber Security.
“Just think about it, when automated industrial systems and PLCs don’t behave the way that they should, the health and safety of your people are at risk, machinery and processes may become unsafe, production output can be affected, and there could be consequences for the communities you operate in or serve.”
However, says Ueckermann, companies can and should continue to leverage the opportunities to manage and streamline business and operations with integrated systems.
“
“The key to protecting your organisation’s industrial automation systems is transparency.”
.“
To start, Ueckermann says organisations should have a thorough understanding of their OT environment. This includes having visibility of all physical and computer assets and how they are connected.
Comprehensive security strategy
Once companies have a comprehensive understanding of the environment and the potential risks, it then becomes necessary to call on technology to assist with controlling access to the environment – which includes both physical and digital assets – as well as put processes in place to protect data.
“Automation and control systems rely on interdependent connectivity and thus require appropriate tools to protect data in the networked systems,” says Ueckermann.
Proactively managing IT/OT threats
Ongoing monitoring to identify possible gaps in security and detect unauthorised access or execution of programmes are also highly recommended. With the correct tools, organisations can proactively pick up vulnerabilities, unauthorised access to systems and data, as well as malware on automation systems and PLCs.
“Education is an integral part of threat management. Systems engineers should have a greater understanding of security and the potential risks for automation control, SCADA and PLC systems. Collaboration between IT, engineering and operations personnel, helps to build a strong team that can respond to threats and incidents quickly and manage risks effectively,” says Ueckermann.
Cyber resilience: How fast can you return to “business-as-usual”?
The capacity to recover from an incident on these systems should also be built-in to restore to “business as usual” as soon as possible. Disaster recovery plans should include strategies for managing the systematic failure of technologies as well as entire systems.
He says standards and guidelines for industrial control systems’ security – also called Industrial Cyber Security – help companies to keep the checks and balances in place that ensure that the highest level of security in control systems are maintained across the enterprise.
Aligning organisations with international best practices
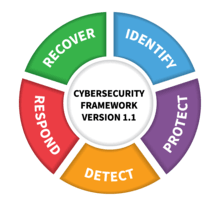
Credit: N. Hanacek/NIST
AVeS Cyber Security works with companies to implement the NIST Framework for Improving Critical Infrastructure Cyber Security. Commonly referred to as the NIST Cybersecurity Framework, it provides organisations with a structure for assessing and improving their ability to prevent, detect and respond to cyber incidents. The Framework uses business drivers to guide cyber security activities and considers cyber security as part of an organisation’s overall risk management processes.
“By implementing the Framework, your organisation will become more focused and proactive about protecting critical assets, both physical and digital. There is a range of technologies that are available to simplify compliance with the Framework to ensure optimal security of data in networks, as well as automation and control systems,” concludes Ueckermann.
