MSIL/Samas.A Threat Notice
Recommended audience for post: Computer network defenders, system owners and administrators.
What is SAMSAM?
SAMSAM (Version 4), also known as MSIL/Samas.A, is a ransomware strain that shares analyses of vulnerabilities on the dark web that cyber actors then use to deploy the ransomware on a network.
How does SAMSAM work?
According to MalwareBytes Labs, SamSam ransomware is a custom infection used in targeted attacks, often deployed using a wide range of exploits or brute-force tactics. Attacks were made on targets via vulnerable JBoss host servers during a previous wave of SamSam attacks in 2016 and 2017. In 2018, SamSam uses either vulnerabilities in remote desktop protocols (RDP), Java-based web servers, or file transfer protocol (FTP) servers to gain access to the victims’ network or brute force against weak passwords to obtain an initial foothold. From there, the ransomware “fun and games” begin for the authors. For everyone else, it’s chaos.
A common thread tying all of these attacks together is the use of the word “sorry” in ransom notes, URLs, and even infected files. It’s made hundreds of thousands of dollars so far, and it’s caused no end of trouble in the US for cities like Atlanta.
I see a ransom note screen on my computer. How do I know it’s SAMSAM?
Here’s what a typical ransom splash screen looks like:
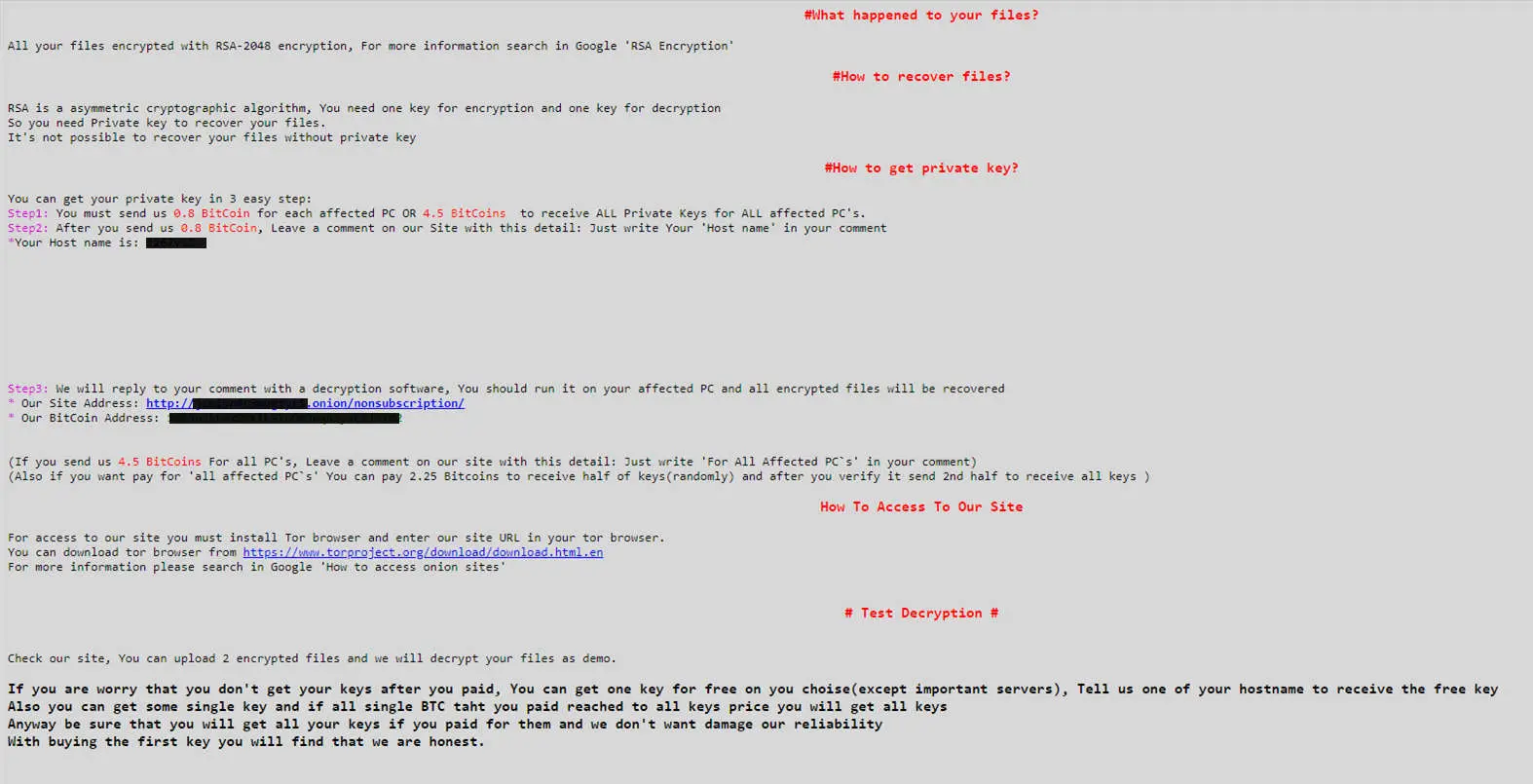
Image by MalwareBytes Labs
The ransom note is quite interesting, giving the option of randomly-selected file encryption (if you don’t pay the full amount). They’ll also unlock one file for free as a token of trust that they will give your files back after payment.
“
In the above ransom note, the hackers demand 0,8 Bitcoins to recover the decryption key for each affected PC – this is about R 43 000 per PC!
x“
According to Symantec’s Security Centre, SAMSAM adds the following extension to the files it encryps: .encryptedRSA
For a list of the ± 328 affected file types, refer to Symantec’s webpage on Ransom.SamSam.
What can I do to check my systems for SAMSAM?
Check your security software logs for the following known detection names:
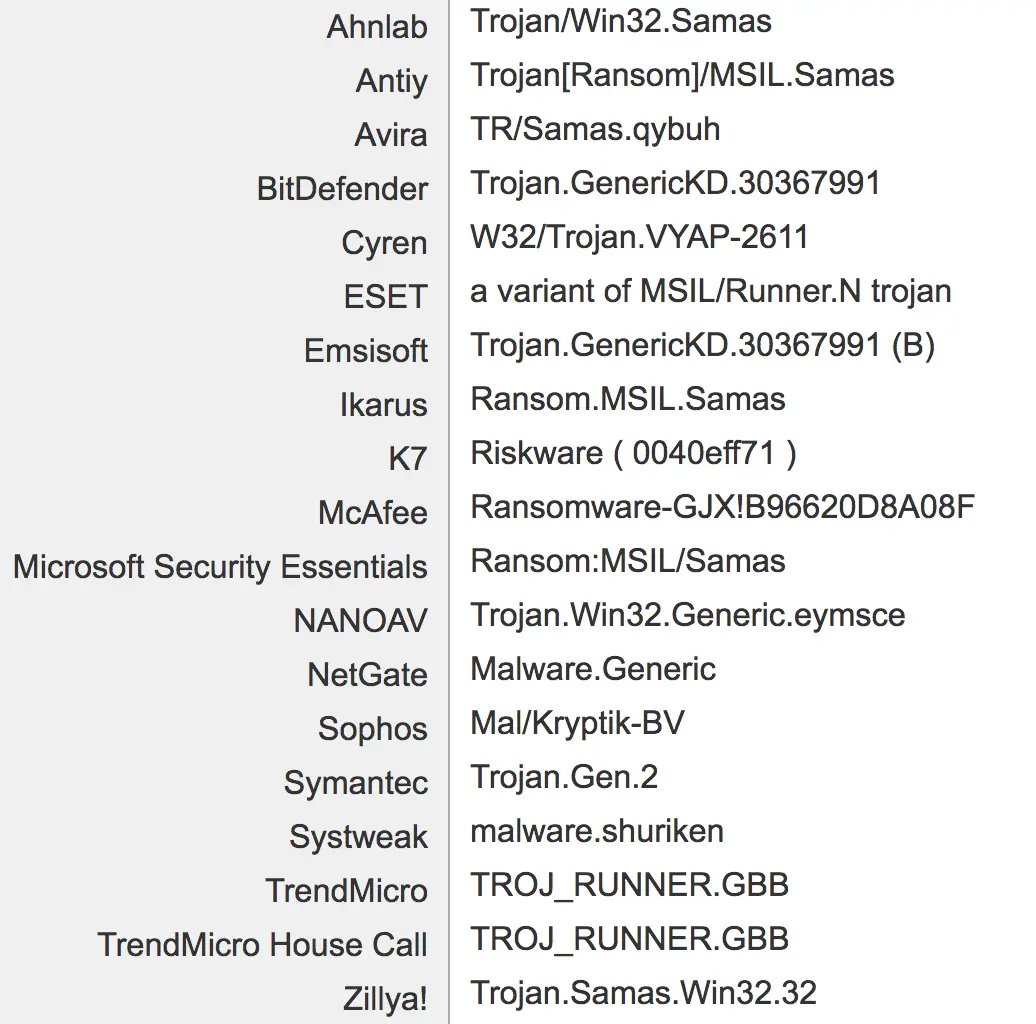
List by US-CERT
What can I do NOW to protect my systems from SAMSAM?
Based on recommendations in the US-CERT’s Malware Analysis Report on SamSam4, you can do the following best practices to strengthen your system’s security:
- Maintain up-to-date antivirus signatures and engines.
- Keep operating system patches up-to-date.
- Disable File and Printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
- Restrict users’ ability (permissions) to install and run unwanted software applications. Do not add users to the local administrator’s group unless required.
- Enforce a strong password policy and implement regular password changes.
- Exercise caution when opening e-mail attachments even if the attachment is expected and the sender appears to be known.
- Enable a personal firewall on agency workstations, configured to deny unsolicited connection requests.
- Disable unnecessary services on agency workstations and servers.
- Scan for and remove suspicious e-mail attachments; ensure the scanned attachment is its “true file type” (i.e., the extension matches the file header).
- Monitor users’ web browsing habits; restrict access to sites with unfavourable content.
- Exercise caution when using removable media (e.g., USBs, external drives, CDs, etc.).
- Scan all software downloaded from the Internet prior to executing.
- Maintain situational awareness of the latest threats and implement appropriate ACLs.
“
Remember: Any configuration changes should be reviewed by system owners and administrators prior to implementation to avoid unwanted impacts.
.“
What else can I do to protect my systems from ransomware like SAMSAM in the future?
According to the United States Computer Emergency Readiness Team (US-CERT), system administrators can do the following to strengthen the security posture of their organisation’s networks:
- Audit your network for systems that use RDP for remote communication. Disable the service if unneeded or install available patches. Users may need to work with their technology vendors to confirm that patches will not affect system processes.
- Verify that all cloud-based virtual machine instances with public IPs have no open RDP ports, especially port 3389, unless there is a valid business reason to keep open RDP ports. Place any system with an open RDP port behind a firewall and require users to use a virtual private network (VPN) to access that system.
- Enable strong passwords and account lockout policies to defend against brute force attacks.
- Where possible, apply two-factor authentication.
- Regularly apply system and software updates.
- Maintain a good backup strategy.
- Enable logging and ensure that logging mechanisms capture RDP logins. Keep logs for a minimum of 90-days and review them regularly to detect intrusion attempts.
- When creating cloud-based virtual machines, adhere to the cloud provider’s best practices for remote access.
- Ensure that third parties that require RDP access follow internal policies on remote access.
- Minimise network exposure for all control system devices. Where possible, disable RDP on critical devices.
- Regulate and limit external-to-internal RDP connections. When external access to internal resources is required, use secure methods such as VPNs. Of course, VPNs are only as secure as the connected devices.
- Restrict users’ ability (permissions) to install and run unwanted software applications.
- Scan for and remove suspicious email attachments; ensure the scanned attachment is its “true file type” (i.e., the extension matches the file header).
- Disable file and printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
