IT Infrastructure Services
Plan. Implement. And get your money’s worth.
Get the right tools and frameworks in place to conduct business in the most efficient way. Your business-critical applications don’t have to let you down.

Ready to protect your business or home?
Get IT & ICS Security services or software from our online marketplace.
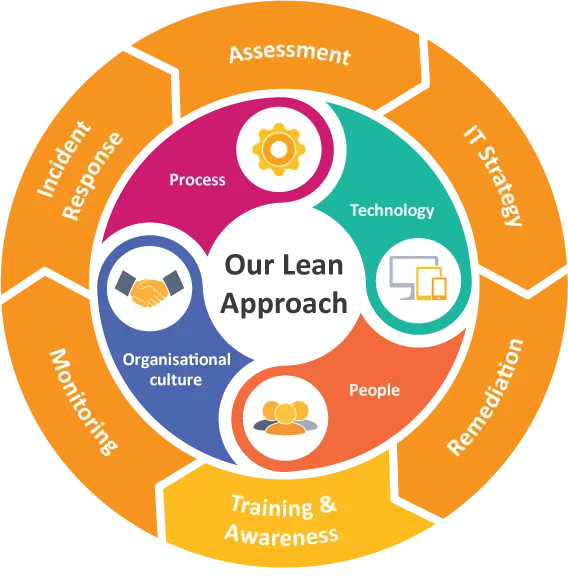
Overview
Our IT Infrastructure practice delivers leading network security and data centre services provides us with a unique set of skills to help businesses assess, plan, design, implement, migrate, secure, optimise and support their IT Infrastructure. As trusted Professional Services Partners to both Dell and Microsoft in various competencies, including Cloud Data Centre, we ensure that our advanced infrastructure is built efficiently with leading technologies.
Benefits
Business-critical applications can now be:
- Available
- Reliable
- Secure
- Scalable
- Well Managed

Online I&T Governance and Management (and many other) Masterclasses

Online I&T Governance and Management (and many other) Masterclasses
Online I&T Governance and Management (and many other) Masterclasses
Deploy Azure Cloud
Migrate your on-premise Exchange and data centre to Office 365 and Azure, for free.

Deploy Azure Cloud
Migrate your on-premise Exchange and data centre to Office 365 and Azure, for free.

Deploy Azure Cloud
Migrate your on-premise Exchange and data centre to Office 365 and Azure, for free.

The project made a huge impact on the business. With phase 1 done, we can now use the planned budget to spend on other important IT projects, because it addressed the production and DR environments for us for the next 5-7 years. Even when one of the suppliers struggled coming to the party with equipment on time, the AVeS team was still super. I’d recommend them 100%.

A-Team
Meet the people who make IT look easy.

A-Team
Meet the people who make IT look easy.






