IT & ICS Security Services
Assess. Measure. And smartly manage your risk.
Your organisation’s unique risk profile and risk appetite will guide your information security strategy. Find out where your cyber risks are and how to outsmart cybercriminals without breaking the bank.

Ready to protect your business or home?
Get IT & ICS Security services or software from our online marketplace.
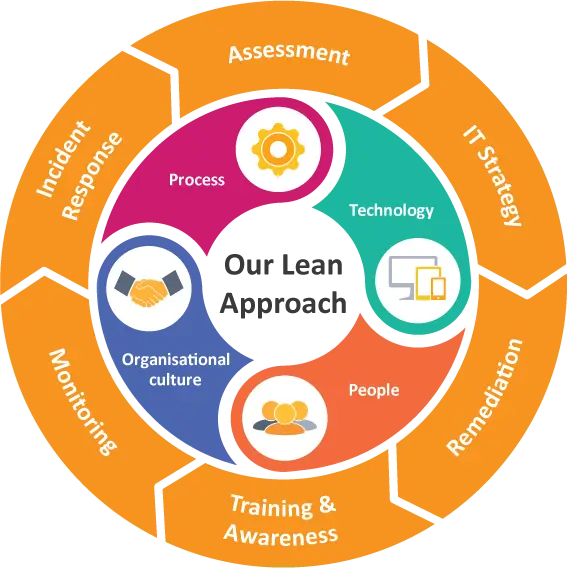
Overview
Our IT & ICS Security practice offers the insight, expertise, and best practices that are needed to gain self-sufficiency in IT Security. Our technical experts combine skill and real-world experience that aim to help the entire IT organisation establish and manage programmes to address and reduce risks against Digital Information Security, Availability, Performance, and Compliance. We believe that focused instructions help build competent and dedicated teams with specialised risk management knowledge and skills.
Benefits
Protect your digital information and industrial environments’:
- Confidentiality
- Integrity
- Availability

Online I&T Governance and Management (and many other) Masterclasses

Online I&T Governance and Management (and many other) Masterclasses
Online I&T Governance and Management (and many other) Masterclasses
Choose Confidence
Get the right Cyber Protection Package for your business with AVeS Cyber Security and Discovery Business Insurance.

Choose Confidence
Get the right Cyber Protection Package for your business with AVeS Cyber Security and Discovery Business Insurance.

Choose Confidence
Get the right Cyber Protection Package for your business with AVeS Cyber Security and Discovery Business Insurance.

We have been dealing with AVeS for a number of years now, and have found them to be one of our best service providers. They are knowledgeable, responsive and thorough in everything they do for us. Nothing is too much trouble, and they attend to our requests promptly.

A-Team
Meet the people who bring smiles to IT managers’ faces.

A-Team
Meet the people who bring smiles to IT managers’ faces.








