I&T Governance Services
Assess. Align. And become IT audit-compliant.
See how your IT department can jump into the fast lane by starting with aligning its objectives to business strategic goals and identifying your cyber risks.

Ready to protect your business or home?
Get I&T Governance services or software from our online marketplace.
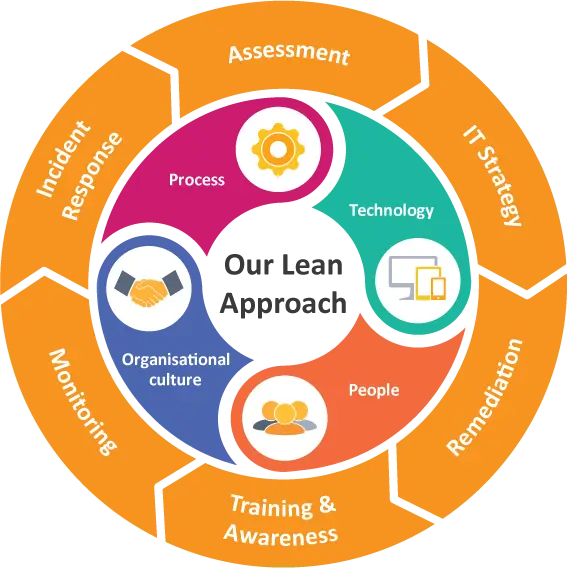
Overview
Our I&T Governance practice offerings aim to uplift the maturity level of IT departments. We help organisations of all sizes align their IT processes, people and technology to the organisation’s broader business objectives, which in turn cuts wastes in time and money. All our strategies are based on King IV’s IT Governance framework, ITIL, COBIT 2019 and ISO 27001, which provides audit-compliant peace of mind.
Benefits
Turn IT into a machine that is:
- Ethical
- Logical
- Standardised
- Internationally measurable
- Audit-compliant

Online I&T Governance and Management (and many other) Masterclasses

Online I&T Governance and Management (and many other) Masterclasses
Online I&T Governance and Management (and many other) Masterclasses
The AVeS Team has been instrumental in the review and update of our ICT policies and procedures. Their combination of skills and experience makes the partnership with AVeS Cyber Security a good one for the IT department at Palabora.

A-Team
Meet the people who make our clients’ governance worlds go round.

A-Team
Meet the people who make our clients’ governance worlds go round.





